Assignment:
Part 1:
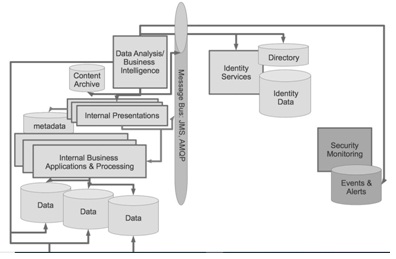
Consider the data flow "octopus," as shown in Figure above. How can the analysis system gather data from all these sources that, presumably, are protected themselves?
Answer the questions with an APA-formatted paper (Title page, body and references only). Your response should have a minimum of 600 words. Count the words only in the body of your response, not the references.
A minimum of two references are required. One reference for the book is acceptable but multiple references are allowed. There should be multiple citations within the body of the paper. Note that an in-text citation includes author's name, year of publication and the page number where the paraphrased material is located.
Part 2:
[X] is an online software company that specialize in selling ad spaces in their parent company's magazine. [X] manages an online database that allows their customers to upload and pay for their business ads for magazine placement. Because [X]'s database needs to connect to the parent company's database, the parent company has requested that [X] system be assessed and verified as secure.
*[X] can be any company name in any line of business.
Your company has designated you to be the lead architect for this project because it's a small company and perfect for your first time. Since you have spent the past 7 weeks in training to be a System Architect, perform your assessment.
Submit your report in an APA-formatted paper (Title page, body and references only). Your report should have a minimum of 600 words. Count the words only in the body of your response, not the references. A table of contents and abstract are not required.
A minimum of two references are required. One reference for the book is acceptable but multiple references are allowed. There should be multiple citations within the body of the paper. Note that an in-text citation includes author's name, year of publication and the page number where the paraphrased material is located.