Course Learning Outcome:
A) Demonstrate understanding and knowledge of IoT key technologies and protocols
B) Critically evaluate data analytics techniques and understand how they are applied in IoT
C) Critically assess data visualization technologies and understand how they affect the implementation of IoT systems
D) Identify non-technical challenges that affect the development and deployment of IoT systems
Problem 1: A simple intrusion detection system
Figure 1 depicts an intrusion detection system composed of a motion sensor, MCU controller, an alarm, a webcam, and an RGB LED light. When a movement is detected, the alarm goes off; the camera switches on; and the light goes red, green, and amber successively.
a) Build in Packet tracer the system in Fig. 1-a. You must submit the pkt file together with your coursework.
b) Demonstrate the behaviour of the system using simulation screenshots.
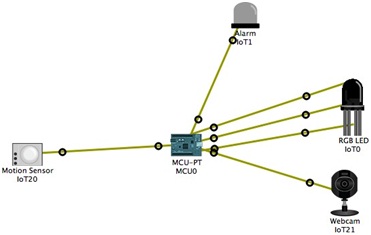
Fig. 1: A simple intrusion detection system
Problem 2: Smart home
Consider the IoT system in Fig. 2. It allows a user to control the IoT devices in their home and their office using a PC at the office or remotely via a smartphone. The IoT devices include a webcam, a motion sensor, a coffee machine and 2 lamps (light). These devices are registered with an IoT server located the cloud. The system enables to monitor and control the IoT devices from a smartphone via a 3G cellular network. Indeed, each of these IoT devices can be turned on/off from a smartphone. In addition, the IoT server is configured so that the webcam and lamp automatically turn on when the motion sensor detects a movement in the home.
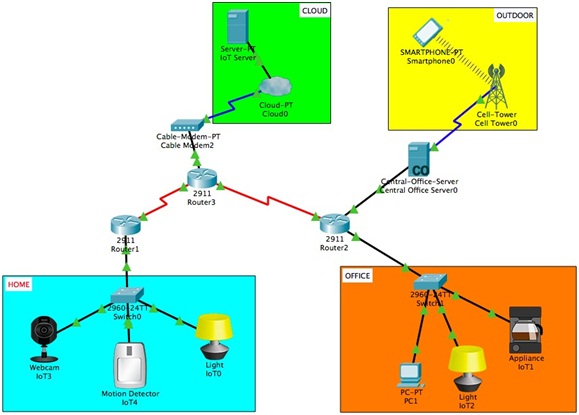
Fig. 2: Smart home
a) Create the IoT system shown in Fig. 2 in Packet Tracer. You must submit the pkt file together with your coursework.
b) Show by simulation that the user can control the IoT devices from a smartphone and the office PC.
c) Show by simulation that the webcam and the lamp turn on when the motion sensor detects a movement.
Problem 3: Data Analytics and Visualisation
a) Trend Analytics and content analytics are 2 types of data analytics. Compare their analytics capabilities based on a critical review of the literature, with clear references. 300 words excluding references.
b) Give critical review of common data visualisation techniques for IoT systems.
300 words excluding references.
c) Consider a popular football stadium that hosts a derby match for local rivals. It is important that fans are kept safe and the match ends with minimal disruption. The stadium management uses video cameras to capture audio, images, and images in strategic places inside and outside the stadium. The aim is to use the resulting data to identify in a timely fashion, incidents that may lead to disruptions - fights, abuse, or stampedes and notify the stewards.
i) What analytics capabilities are needed to realize the solution?
ii) What analytics type should be implemented?
iii) What combination of tools can be used to implement the solution?
Problem 4: Design your own IoT system
a) Propose your own IoT system for a specific application. This must not be a close version of any of the systems described in this coursework. Give a detailed description of the functionalities of your system.
b) Give a detailed critical literature review of existing related systems with clear references, and demonstrate the novelty of your proposed system. (5%) 600 words excluding references.
c) Identify and justify the technologies needed for the implementation of the proposed IoT system.
d) Implement your system in Packet Tracer. You must submit the pkt file together with your coursework.
e) Give the simulation in Packet Tracer (screenshots) of the main functionalities of your system.
f) Identify and justify the data analytics and visualisation techniques that apply to your proposed system.
Problem 5: Modelling and Analysis
A Simple Infostation-based Communication System
An infostation system is an infrastructural system concept that provides many-time, many- where wireless data services. This case study is a simple context-aware infostation-based system, which allows users to exchange text messages using mobile devices such as laptops, smart phones or tablet computers. Typically, an infostation system comprises one central infostation centre (ISC) and many wireless access points, called infostations (ISs), deployed at key positions to maximize coverage. The ISs are physically connected to the ISC via network cables.
In this example we consider a university that has 2 campuses A and B. Each campus has its own infostation system (with one ISC and many ISs). The ISCs of the 2 campuses are physically connected by cables to a network hub to enable users located at different campuses to exchange messages, as depicted in Fig. 3.
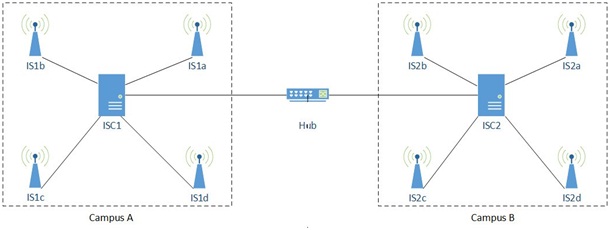
Fig. 3: An infostation-based communication system
An infostation is aware of any mobile device within its range and is able to interact with the device, e.g. by exchanging messages. A user within the range of an infostation can send or receive text messages using a mobile device. For the sake of simplicity, we assume that a text message has the following format: (sender, recipient, message). E.g. send (bob, alice, hello) means bob is the sender, alice the recipient and hello the message.
Once an infostation receives a text message, it checks if the recipient is within range in which case it forwards the message to the recipient. If the recipient is not within the range of that infostation, the infostation forwards the message to the infostation centre it is connected to.
An infostation centre is aware of all the infostations connected to it and subsequently of all the devices within the ranges of these infostations. However, an infostation centre has direct communications only with the infostations and the network hub connected to it. When an infostation centre receives a text message from an infostation, it looks for the infostation where the recipient is located and forwards the message to this infostation. The infostation where the recipient is located then forwards the request to the recipient mobile device. If the recipient is not found in one campus, the message is forwarded via the network hub to the infostation centres of the other campus for delivery.
When the network hub receives a message from one ISC, it sends the message to the other ISC.
What to Do
You are required to model the Simple Infostation-based Communication System in the Calculus of Context-aware Ambients (CCA) and to analyse this model using the CCA simulator ccaPL. We assume there are four ISs and one ISC in each campus, named as in Fig. 3 (IS1a, IS1b, ...) and two user mobile devices (Bob's and Alice's). Each of these entities and the network hub can be modelled as an ambient in CCA. We say that a user's mobile device is in the range of an infostation IS if the ambient modelling that mobile device is a child ambient of the ambient representing the infostation IS.
Modelling
a) Give a ccaPL specification of the ambient modelling the infostation IS1a.
b) Give a ccaPL specification of the ambient modelling the infostation IS2a.
c) Give a ccaPL specification of the ambient modelling the infostation centre ISC1.
d) Give a ccaPL specification of the ambient modelling the infostation centre ISC2.
e) Give a ccaPL specification of the ambient modelling the network hub.
Analysis:
Assume Bob is initially in the range of the infostation IS1a in the Campus A. He then moves from IS1a to IS1d, sends a hello message to Alice, and finally moves to IS1c. In the meantime, Alice is in the range of the infostation IS2b in the Campus B, but on the move to IS2c and then to IS2a. She will receive Bob's message at some point during this journey. For simplicity, it is assumed that a single ambient called bob represents Bob and his mobile device. Similarly, Alice and her mobile device are modelled as a single ambient alice.
6) Give the specification of the ambient representing Bob's mobile device.
7) Give the specification of the ambient representing Alice's mobile device.
8) Give the simulation results of the system for the scenario described above. These results must include: (i) the listing of the execution output; (ii) the corresponding communication graph; (iii) the corresponding behaviour graph; and (iv) a clear explanation of the execution output.
Our professional Internet of Things Assignment Help tutors are highly competent and can write on any topic of any complexity level. They can even write a custom-made assignment paper as per the requisites of the student's at the most feasible prices.
Tags: Internet of Things Assignment Help, Internet of Things Homework Help, Internet of Things Coursework, Internet of Things Solved Assignments, Data Analytics and Visualisation Assignment Help, Data Analytics and Visualisation Homework Help, Modelling and Analysis Assignment Help, Modelling and Analysis Homework Help
Attachment:- Internet of Things.rar